Rocky the raptor here, RPost’s cybersecurity product evangelist. I’m feeling somewhat famous, having been profiled in the news yesterday and having my kind (Raptor) plastered as the brand of the newest and coolest Cyber Command Center. In this command center, raptors hunt for mangy bait on phish lures, and AI agentically strip the bait off the hooks before human friends get caught up in cybercriminal fangs. (Read news / more here).
Where do we raptor cybersecurity specialist focus? In the red zone. The danger zone. The unstructured risk zone of today. Let me explain.
 Green zone. In military terms, the green zone is the home base with a strong perimeter security that protects those inside from threats. Those working inside the green zone can (in theory) go about their business without concern of risk. Those working to protect the perimeter of the green zone do so tirelessly with all the tools one can afford. Defending the green zone is certainly not trivial. RMail Gateway (depicted here with the green R logo in homage to its focus on protecting the green zone of a company) is the most sophisticated cybersecurity technology that protects the endpoints, the perimeter of an organization against inbound threats and outbound data leaks (traditional DLP).
Green zone. In military terms, the green zone is the home base with a strong perimeter security that protects those inside from threats. Those working inside the green zone can (in theory) go about their business without concern of risk. Those working to protect the perimeter of the green zone do so tirelessly with all the tools one can afford. Defending the green zone is certainly not trivial. RMail Gateway (depicted here with the green R logo in homage to its focus on protecting the green zone of a company) is the most sophisticated cybersecurity technology that protects the endpoints, the perimeter of an organization against inbound threats and outbound data leaks (traditional DLP).
RMail Gateway is the Best in Endpoint Security, Green Zone Protection.
But wait, where do most of these threats that attack, the most sophisticated, originate and how are they successful? Cabals that live outside of the green zone, in the wild, and scheming day and night on how to best infiltrate to cause the most damage. These cabals are doing their reconnaissance, digging into compromised email accounts at third parties (outside of the green zone) that are working with content (email, documents, eSign transactions, file shares, data rooms) of the people inside the green zone. This content must leave into the wild in the normal course of business. This is a target of the cabals, to intercept, evaluate, learn context, to power up hyper targeted, hyper contextual lures and trickery.
The Best (Green Zone) Defense is a Strong Offense.
To go on offense, RAPTOR™ AI (I like to think, named after me, Rocky, and my buds 😉) goes beyond the endpoint and actively hunts for these cybercriminal cabals baiting their phishing hooks with juicy, contextual phish bait to lure green zone workers to make mistakes.
RAPTOR™ AI, in short, is Security Beyond the Endpoint. Red Zone Security and Intelligence.
Let me explain (for those who are interested in details…keep reading. To respect those heading out for the beach early, you may drop off now 😉.)
RAPTOR™ AI:
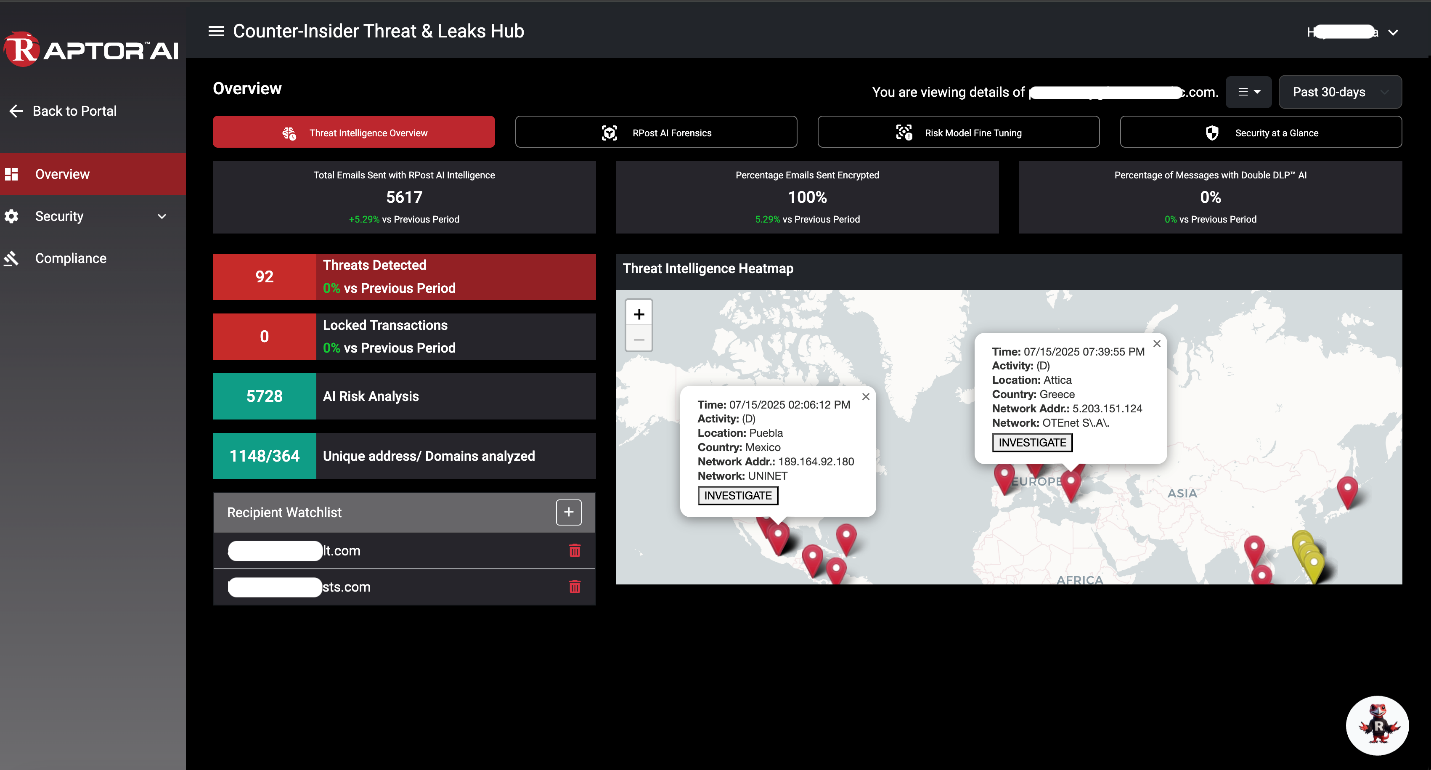
RPost solves for these with its PRE-Crime™ preemptive cybersecurity solution powered by RAPTOR™ AI. By the way, Gartner Research recently named RPost a Visionary for its PRE-Crime preemptive cybersecurity and Aragon Research recently named RPost a worldwide Leader in Intelligent Enterprise Content Management.
Why are these important? To recap…
In summary…
Value of Pre-empting Leaks before Seen. If there is a leak of sensitive information on unauthorized devices, there is a cost due to the risk of exposure, reputational issues, strategic risk of threat actors gaining advantage for a targeted or long-term attack, and also the staff cost to investigate and remediate (clean, wipe) all devices that had touched the leaked sensitive information.
Remember, one must differentiate between Green Zone (Defense) Security and Red Zone (RAPTOR, Offense) security. You need both, considering today’s cyber threat environment.

February 27, 2026

February 20, 2026
.jpg)
February 13, 2026

February 06, 2026

January 30, 2026