Rocky the Raptor here, your sharp-clawed cybersecurity evangelist, here to rip apart some old myths about Man-in-the-Middle (MITM) attacks - those sneaky tactics most people think they understand, but few realize just how far they’ve evolved.
When you hear “MITM attack,” you probably imagine a cybercriminal lurking on a public Wi-Fi connection and silently eavesdropping on emails to intercept a password or wire transfer instructions.
And for a long time, that was spot-on. But today these Man-in-the-Middle attacks have evolved into something much more cunning, much harder to detect, and far more dangerous.
I wrote about MITM in my earlier post, where I talked about what I’ll now call the “Classic” MITM approach. In this post, we’ll track the evolution of these attacks.
Man-in-the-Middle Attacks – From Classic to Advanced
As I explained earlier, in a classic MITM attack scenario, sending an email was like mailing a postcard. Any cybercriminal “wedged in the middle” could read your message, steal sensitive data like login credentials or wire transfer details, and alter messages. But as email encryption like TLS became more common, this technique lost its charm.
Cybercriminals then adapted with modern MITM tactics like TLS manipulations to silently downgrade encrypted email traffic to plain text and access sensitive content. Though sneakier than the classic versions, this method was a lot of work for cybercriminals for a limited payoff.
Today, we’re in the advanced stage of Man-in-the-Middle Attacks, where cybercriminals are simply “taking over” the email accounts of trusted third-party systems, like vendors, suppliers, and even your clients.
These parties are vulnerable because most of them often don’t have the budget for enterprise-grade security, or have weaker defenses, while sitting on a pile of sensitive communications and deal flows.
Once inside, the cybercriminals embed themselves as sleeper agents inside inboxes. They don’t act right away. Instead, they:
And because these emails originate inside a trusted account, even the sharpest human eye or traditional security tool will struggle to detect them.
This is what I call MITM reimagined in a most deadly form.
This technique fuels some of the most devastating Business Email Compromise (BEC) and Ransomware attacks today.
It’s not just a man-in-the-middle anymore -- it’s a man already inside the system!
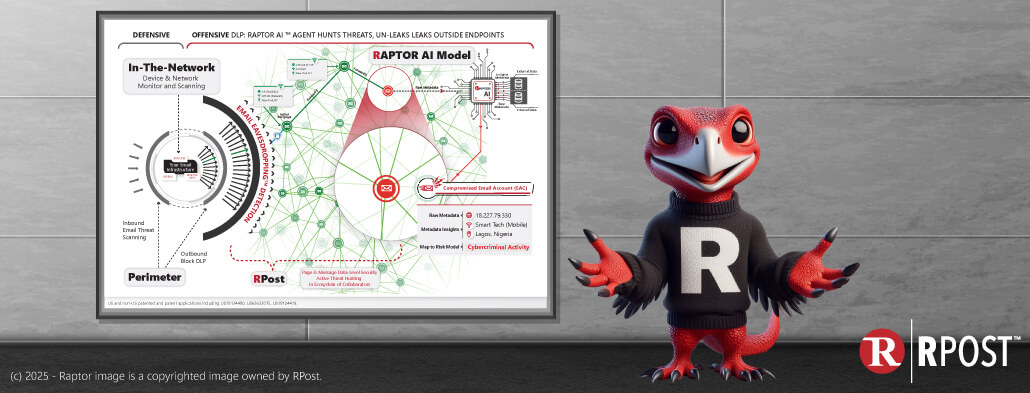
Why RAPTOR AI Is the Only Defense
Here’s the hard truth: endpoint-focused defenses can’t see these attacks. Your firewalls, spam filters, and antivirus tools stop threats at your perimeter. But today’s cybercriminals are inside your clients or partners’ systems, beyond your line of sight – BEYOND your endpoints where you have zero visibility today or control (but for RAPTOR™ AI 😉).
RPost’s RAPTOR AI technology uses advanced analytics to spot the telltale patterns of MITM-style attacks, even when the attacker is:
By correlating signals across millions of interactions -- IP data, geolocation, risk codes, and more -- RAPTOR AI can detect Man-in-the-Middle Attacks in progress, giving you the chance to act.
Bottom line: If you can’t see into your third parties, you’re flying blind. RAPTOR AI isn’t optional anymore; it’s essential. Get in touch with us to learn more.

February 20, 2026
.jpg)
February 13, 2026

February 06, 2026

January 30, 2026

January 23, 2026