
We’ve talked a lot about the hydra of BEC (business email compromise) attacks recently due to the increasing share of these types of attacks within the universe of cybercrime that employ multiple techniques to lure users into sending money to the wrong person (to the cybercriminal). Recall that the hydra possesses many heads, and for every head chopped off, it would regrow two new heads. If your email system is not up to snuff, then fixing only one of these BEC attack vectors can easily lead to increased and potentially more devastating attacks.
[Join next week’s Optimize!22 product showcases on BEC email security, document rights management, and eSignatures – read more here]
Now we have another, less mythical animal to introduce: the wolf. Recall the old fable where the shepherd boy, in an apparently sad bid for attention, kept crying out “wolf!” to the villagers when there was no wolf anywhere near the herd. One of the villagers famously said to the boy, “save your frightened song for when there is really something wrong!” When the boy finally did see the wolf, well, you know the rest of the story.
(More recently, there has developed a school of thought that places blame on the villagers in the fable for leaving such a self-absorbed attention seeker in charge of the herd. In other words, if we left one of the Real Housewives in charge of NORAD, wouldn’t it be our fault if we found ourselves looking up from a pile of radioactive ash?)
Many email gateways have alerting capabilities for reply hijacking and anti-whaling. This is good. However, they will place stamps on emails regardless of whether there is a mismatch in the email domain—a clear sign of an incoming BEC attack.
To illustrate this more clearly, can you easily tell the difference between these three stamps (i.e., can you spot the real wolf?)

If yes, congrats, but are you prepared to put in the work every time you respond to one of the hundred or so emails you send a day? These methods distract users and cause them to burn brain cells unnecessarily, studying details in text versus seeing an alert when there is an actual issue–a mismatch in stated vs real email addresses.
You’d be like the villagers getting tired of having to go up and down the hill to see if the boy was telling the truth. Meanwhile, the wolf is still lurking. Plus, if the wolf were ‘smaller’ (say, only one letter off), this does little to minimize human error, as most humans would not see the distinction every time.
An even more sophisticated version of this type of impostor email threat is sent through the legitimate client’s email account once there is an email account compromise, and there is ZERO level of inbound security gateway or firewall filtering that will alert or block it. Hence, the hydra effect of BEC attacks.
As we’ve said in previous Tech Essentials, you need RMail’s layered technology approach — on top of what you already have — to defeat these and other BEC attacks, even if you have inbound security buttoned up. Only RMail offers the integrated features that can foil BEC attacks leveraging AI and real-time Lookalike Domain™, Reply Hijack™, and Email Eavesdropping™ alerts without those “cry wolf” stamps.
Know More
How to Recall an Email in Outlook
For contrast, here is an example of the approach of the RMail Lookalike Domain alert:
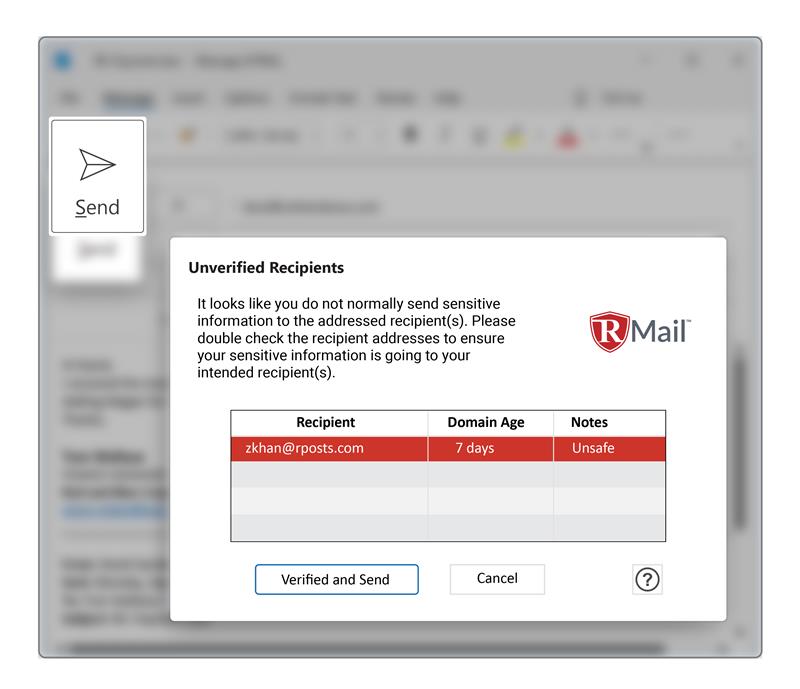
RMail takes out so many hydras and wolves that PETA may want to take notice! Please contact us to learn more about RMail and all its BEC-beating features.
And please note that RPost’s Optimize!2022 global e-security and eSign user conference (click here to read more) is still going on, but time is running out to register. This year’s unique format includes web sessions spaced throughout the month plus in-person expert tours across the Americas and Europe.
Also note that you can re-live our October 18 Florida Bar CLE Cybersecurity Webinar sponsored by RPost and obtain 1 Full Free Credit.

February 20, 2026
.jpg)
February 13, 2026

February 06, 2026

January 30, 2026

January 23, 2026